Privacy must be kept when analyzing data, it is enforced by law. To main privacy, strategies have been made:
De-identifying data
To de-identify data, it refers to removing any personal information and identifiers such as names and birthdates that are tied personally to the participant.
| Given Name | Surname | Height | Weight |
|---|---|---|---|
| Charlotte | Micelli | 145 | 48 |
| Candace | Fock | 153 | 40 |
| Table above shows a data set that hasn’t been de-identified yet. |
| Participant | Height | Weight |
|---|---|---|
| 001 | 145 | 48 |
| 002 | 153 | 40 |
| Table above shows a data set that has been de-identified. |
However, de-identifying may not always work due to the fact that researchers may know the participants well, or the data itself may also lead to the identification of the participant.
Physical and software security controls
There are laws to ensure that data must be kept secure and confidential, which prompts the question, how should we store our data?
Physical controls
- Hard copies must be kept secured.
- Usage of passkeys ensure only the right people can access the data.
- Even something like the placement of monitors may lead to leaks.
Encryption
Encryption refers to the process of translating data into ciphertext that’s unreadable without a “key” to translate it back to readable.
Backups
Backups are essential in ensuring that risks won’t do any permanent or long-lasting damage to data. Backups come in 3 forms:
| Full backup | Differential backup | Incremental backup |
|---|---|---|
| A full backup is just like the name entails. It creates a completely new copy of everything, including things that are already backed up. It is a slow, but extremely safe method. | A differential backup only backs up files that have been changed since the last full backup. | An incremental backup only backs up files that have been changed since the last incremental backup. |
Usernames and passwords
An identifier with an unique password that the only the user should know. According to Nelson.net, your password should be:
- at least 8 digits long
- include non-alphabetical characters
- cannot be guessed
- be changed every month
Firewall
A firewall is a tool that filters incoming network traffic, flagging potential sources of harm such as malware and viruses. A firewall can be used to also direct and restrict access from certain users in the network, so an employer can use a firewall to restrict their employees from accessing a payroll documentation for example.
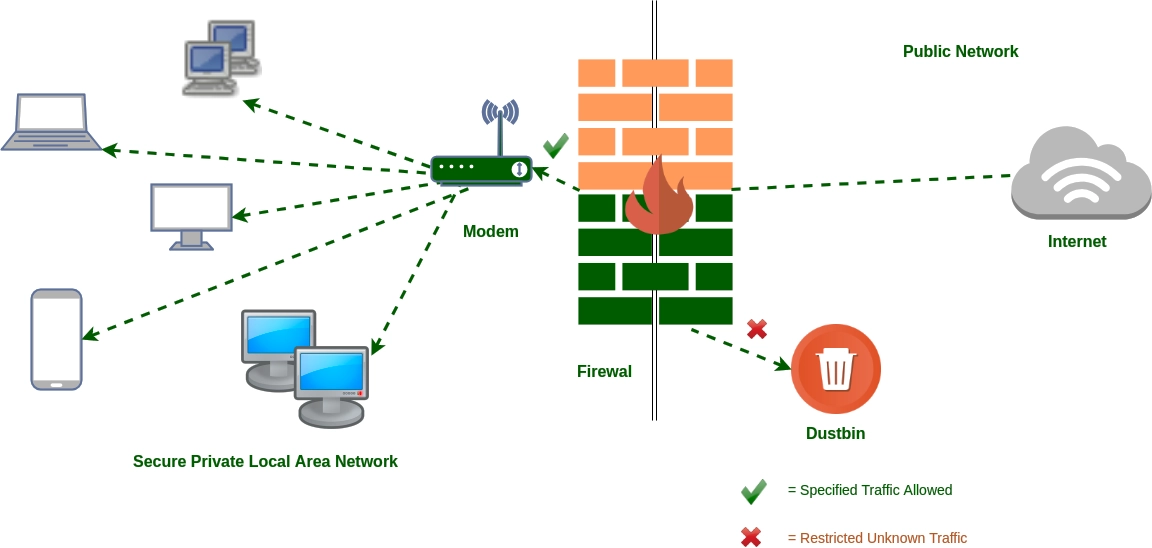 This works by applying “rules” and filtering phrases, file types and more in data packets. For example, my self-hosted API that uses Cloudflare Zero Trust as a security provider has a rule that prevents anyone from authorizing their account on my API.
This works by applying “rules” and filtering phrases, file types and more in data packets. For example, my self-hosted API that uses Cloudflare Zero Trust as a security provider has a rule that prevents anyone from authorizing their account on my API.
Malware protection
Virus protection software like Windows Defender, Norton Antivirus and Avira are all software used to identify and remove malware, viruses and other malicious software that may invade and steal personal information, destroy networks and more.
Whitelists and blacklists
Whitelists are lists that contain elements a network can only interact with, blacklists are lists that contain elements that a network cannot interact with. These lists may contain IP addresses, domains, devices, or programs.
Australian Privacy Principles (APPs)
The Australian Privacy Principles (APPs) are a set of 13 principles that govern the collection, use, disclosure, storage, and security of personal information in Australia. They apply to all organisations and agencies covered by the Privacy Act 1988. The APPs are designed to protect individuals’ privacy while allowing organisations to use personal information for legitimate purposes.
Some states also have their own private privacy laws such as Victoria’s Privacy and Data Protection Act 2014 (PDPA), but they mostly share the same purpose.
The APPs oversee the handling of personal information by:
- Australian and Norfolk Island government agencies
- all private health service providers
- businesses with over $3 million turnover annually
- businesses involved with trading personal information
Some of the key principles include:
- Principle 2: All personalized data must be de-identified. This means that individuals dealing with organisations that trade with private information must be given the option to either remain anonymous, or given a random name/pseudonym.
- Principle 6: Information from individuals must not be used for any other purposes but the original intentions.
- Principle 11: Information from individuals must be actively kept secure and held from unauthorized usage, modification, or disclosure. Once the original purpose has been accomplished, the data must be properly destroyed and de-identified.
The APPs are principles-based, which means that organisations have flexibility to tailor their personal information handling practices to their specific needs. However, organisations must still comply with the spirit and intent of the APPs.
The APPs are enforced by the Office of the Australian Information Commissioner (OAIC). The OAIC can investigate complaints about breaches of the APPs and take enforcement action, including issuing fines.
Full list:
| APP No. | Principle | Description |
|---|---|---|
| 1 | Open and transparent management of personal information | Organisations must be open and transparent about how they handle personal information. |
| 2 | Anonymity and pseudonymity | Individuals have the right to remain anonymous or use a pseudonym when dealing with organisations. |
| 3 | Collection of solicited personal information | Organisations must only collect personal information that is necessary for their functions or activities. |
| 4 | Dealing with unsolicited personal information | Organisations must take reasonable steps to destroy or de-identify unsolicited personal information. |
| 5 | Notification of the collection of personal information | Organisations must inform individuals about how their personal information will be used and disclosed. |
| 6 | Use or disclosure of personal information | Organisations must only use or disclose personal information for the purposes for which it was collected, unless the individual consents or the law permits. |
| 7 | Direct marketing | Organisations must not use personal information for direct marketing purposes without the individual’s consent. |
| 8 | Cross-border disclosure of personal information | Organisations must take reasonable steps to ensure that personal information is protected when it is disclosed to overseas recipients. |
| 9 | Adoption, use or disclosure of government-related identifiers | Organisations must not adopt, use or disclose government-related identifiers without the individual’s consent or unless the law permits. |
| 10 | Quality of personal information | Organisations must take reasonable steps to ensure that personal information is accurate, up-to-date, complete, relevant, and easy to understand. |
| 11 | Security of personal information | Organisations must take reasonable steps to protect personal information from unauthorised access, use, modification, disclosure, or loss. |
| 12 | Access to personal information | Individuals have the right to access their personal information held by organisations. |
| 13 | Correction of personal information | Individuals have the right to request that organisations correct their personal information if it is inaccurate, out-of-date, incomplete, irrelevant, or misleading. |